Cisco has prepared an annual overview of the cyber security segment. Among the top trends, the Cisco Talos Year in Review found that 2023 saw a resurgence of ransomware attackers.Cisco Talos is one of the largest threat intelligence organizations in the world. The annual Talos Year in Review report sheds light on the current trends and future threats that can be expected in 2024. David Libenberg (David Libenberg), Head of Strategic Analysis at Cisco Talos, is responsible for analyzing the most powerful cyberattacks and trends in the threat landscape at Cisco. He talks about the features of this year’s report, and how organizations can strengthen their defenses in 2024.
Cybersecurity is a rapidly evolving and changing field. Conducting retrospective analysis helps to analyze these changes in the current course of events, as well as to predict the future.
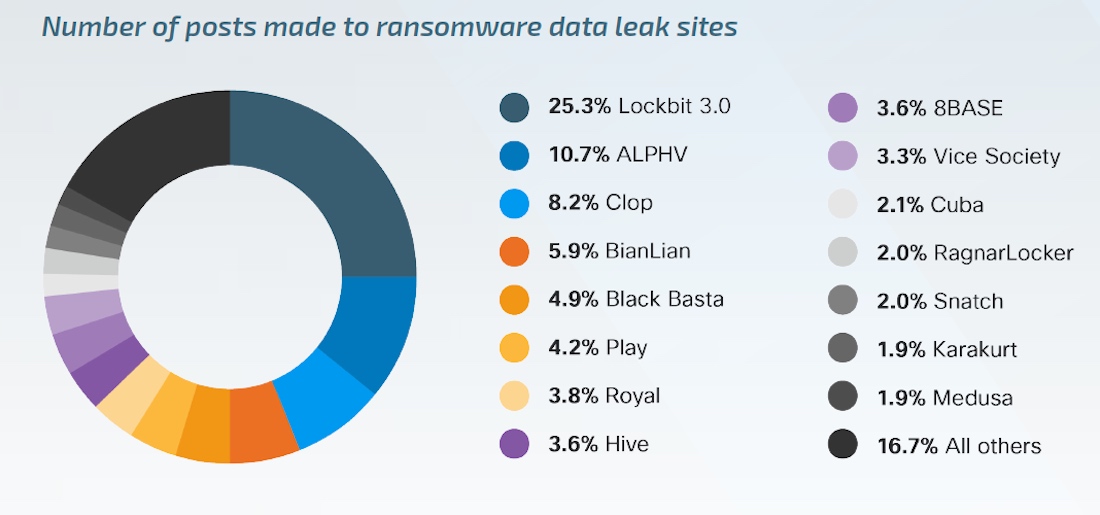
Ransomware is at its peak again
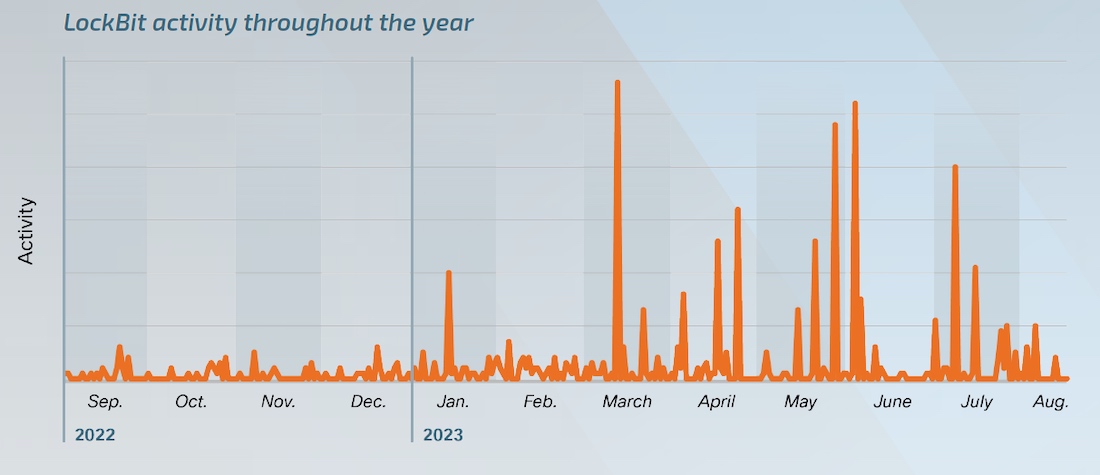
Ransomware is once again the top threat this year. The most active group, as last year, remains LockBit. Three more—ALPHV, Clop, and BianLian—are also very prominent. These groups exploited multiple Zero Day vulnerabilities on various platforms. This is something that can be categorized as APT – Advanced Persistent Threats. An interesting trend: Clop demonstrated a high degree of training and resourcefulness.
One important trend is that many well-known ransomware groups, such as Babuk, BianLian, and Clop, have moved to open blackmail and extortion. Attackers don’t encrypt anything, they just steal data and threaten to leak it. In the second quarter of 2023, such direct extortion cases accounted for almost a third of all incident response statistics. And in terms of number, they even exceeded the number of incidents with extortion software. Additionally, this trend was exacerbated by the fact that these large groups of attackers had the source code of their builders and other tools leaked, which later allowed less experienced attackers to modify the code and create and deploy their own ransomware suites.
Access vectors
Among the initial access vectors, the following were most often used:
- exploiting vulnerabilities in public programs;
- using compromised or valid credentials;
- phishing
The analysis showed that attackers are constantly exploiting old software vulnerabilities, some of which are more than 10 years old. This suggests that organizations should implement a healthy and effective patch and update program.
If companies continue to rely on legacy infrastructure with known vulnerabilities, these will be used as primary network entry points. A modernized network is the best answer. However, even older equipment, if regularly updated with software, has a better chance of protection.
About the responsibility of employees and the general culture of the company
Individual employees and corporate culture can certainly contribute to a healthy cybersecurity ecosystem. Each employee must adhere to company security policies, avoid reusing passwords or hashed passwords, take appropriate precautions when working remotely, and be alert to social engineering attacks. To improve corporate culture, frequent training and testing is necessary. It is important that specialists responsible for internal security should be able to effectively influence company policy.
Security experts should implement multi-factor authentication and network segmentation. After all, businesses want to protect their assets as reliably as possible and be sure that access management and credentials are secure. It is important for an IS department to have an incident response plan in place to respond quickly and effectively to an event, rather than making up a plan on the fly.
The role of AI in the field of cyber defense
Technologies based on artificial intelligence play an increasingly important role in the field of social engineering protection. After all, they make it possible to create new means of protection even faster. This is a rapid technological race that adds complexity to already known classic security problems. Attackers use artificial intelligence to generate sophisticated, persuasive and targeted lures. On the other hand, it is possible to create tools for cyber protection based on AI: in particular, Talos is currently developing a machine learning model that helps to detect the compromise of corporate e-mail. Also, machine learning can detect misinformation on the Internet. So AI opens up wide opportunities for both parties.
Cyber threats from the state of the aggressor
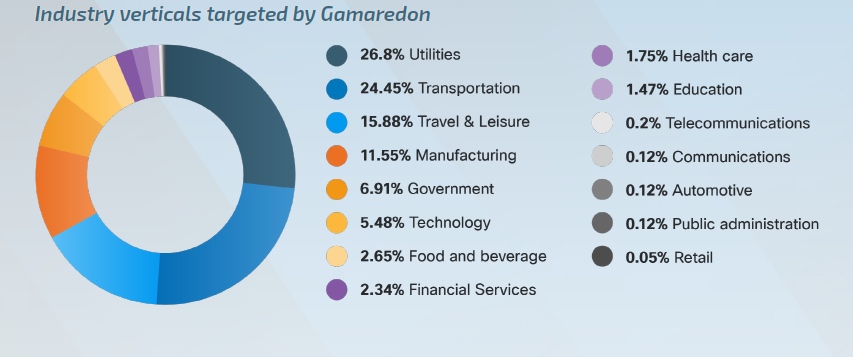
A separate section of the report is devoted to the analysis of the activity of cybercriminals from Russia. The country-linked APT groups Gamaredon and Turla continue to be major threats in this space, updating aspects of their attacks and toolkits to support their TTPs, despite international efforts to combat the Russian cyber threat, it said.
Cisco Talos has been closely monitoring activities related to Gamaredon, an APT believed to be a group of government-backed Russian agents based in Crimea. While the group has focused its cyber espionage efforts against Ukrainian organizations in recent months, it also attacks organizations around the world, but its victimology is less focused compared to other Russian APTs operating in this space. Turla also carries out long-term espionage and data exfiltration, which is in line with Russian intelligence priorities. This APT group is attributed by the US government to one of the divisions of the FSB. Unlike Gamaredon, which Talos observed targeted a number of sectors in 2023, Turla is known for much more targeted operations against a smaller number of strategically important entities. Turla, publicly believed to be acting on behalf of a different FSB unit than Gamaredon, is believed to be capable of compromising a much wider range of organizations around the world, but restricts its operations to what it believes are high-risk targets. value.
Forecasts for 2024
Ransomware will continue to spread. However, attackers will use bootloaders more actively. This is a type of software that can be purchased on the dark web or obtained from the open source. In 2023, the volume of application of loaders increased and will increase in the current year.
One of the most popular bootloaders of the last year, Qakbot, was recently effectively defunct. But several new downloaders appeared. As for APT (advanced persistent threats), Cisco continues to observe how Ukraine is becoming a target of highly professional hacker groups associated with the Russian Federation and China. They target organizations related to critical infrastructure and essential services in industries of strategic importance.

However, last year there were positive moments that add optimism for this year as well. The qualification and cooperation of specialists in the field of cyber security is growing. In 2023, Cisco announced the creation of the Network Resilience Coalition, which helps identify attackers and protect organizations from cyber attacks, particularly in Ukraine. This coalition has achieved tremendous success in the fight against cybercrime.
Source: https://ko.com.ua/